If you are looking for a system to quickly create or transform users’ work from local to remote Working?, this guide will certainly help you a lot.
This guide aims to provide information to transform an “old-fashioned” company into a Remote Working company in a simple way, using free tools and without distorting user operations.
Tools to Accelerate Remote Working
Through the implementation of a VPN, the activation of the RDP protocol and the S.O. pfSense or OPNsense, allow users located anywhere in the world to connect to the company computer system and work exactly as if they were sitting in front of their PC.
All this without upsetting the company computer system, modifying the user modus operandi as little as possible and using free tools.
So the scenario that will be analyzed and implemented will be the following:
- Configuration of a firewall that will act as a VPN server (or VPN concentrator) with pfSense or OPNsense.
- The company and remote devices must be connected to the Internet.
- We will configure remote devices to connect to the corporate network via a secure VPN connection. Users will reach their workplace (for example their PC or MAC) via the RDP protocol, working as if they were sitting in the office, in their place.
In addition, we will pay particular attention to the problem of bandwidth consumption, which through the tools used will be optimized to the maximum.
Often, the problem of “low bandwidth” deters from the implementation of these technologies in companies.
In this guide, we will address the problem by using tools that require and use a minimal amount.
Once all these tools have been implemented, we will make some reflections and optimizations on the security side.
We will limit access based on what the user must do and on time slots.
We will also dedicate ample space to the choice of the data encryption algorithm according to the hardware device we have available.
Once the whole implementation is finished we will move on to the general safety test of what we have just created. Using a ready-to-use solution, we will scan the entire network for security holes.
This tool will allow us to find and close them.
Finally, we will move on to the implementation of a 3CX VOIP telephony solution that will allow us to stay in touch both by telephone and with WebMeeting with colleagues, customers and suppliers.
Software environment:
pfSense® 2.4.x, Windows 10, Mac OS X, 3CX 16.X
Hardware environment:
For the Firewall / VPN Server we have chosen this device: https://www.miniserver.store/appliance-small-utm-2
This appliances could be an excellent choice for managing from 5 to 25/30 simultaneous VPNs.
VPN: Types, Differences, Advantages and Disadvantages.
In recent years and never as in these days we are talking about Remote Working. One of the technologies necessary to allow this type of activity is undoubtedly the VPN.
A VPN (Virtual Private Network) is a “virtual connection” that allows you to create a private network between two or more devices, which are not found in different networks.
This virtual link is called a tunnel.
In fact, a VPN allows us to connect directly to our office network, and work as if we were physically there, through the creation of a tunnel
We will now see what types of VPN exist and the main differences.
The first big distinction is:
- Access VPN or, as pfSense calls it “Road Warrior”.
- VPN Site to Site
Access VPNs allow a remote user to access the destination network, such as the office network.
The peculiarity of the access VPN is that it is very “smart“, that is, the remote user can open and close the tunnel every time he has to connect to the office network; but not only: the access VPN allows mobility, i.e. the remote user can create a tunnel from any public network that allows it (home network, library, cellular hotspot etc …).
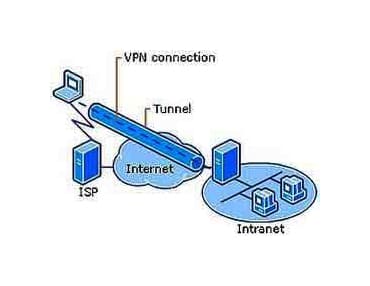
The Tunnel is created on the public network (Internet) which is not in the least aware of this Tunnel (Overlay model).
Site to Site VPNs are the VPNs that allow communication between two corporate offices (for example, the corporate office in Turin with the Milan office).
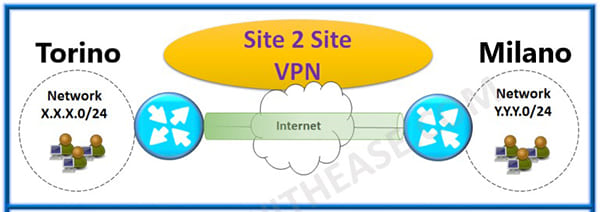
Thanks to the Tunnel, the two offices are as if they were in the same private network being able to communicate without problems.
Unlike the access VPNs, this solution is intended to be permanent, i.e. the tunnel remains constantly active between the two offices, as there is no need to guarantee mobility.
This guide will focus on the VPNs that allow Remote Working and therefore to allow access to a remote user to the corporate network, or the Road Warrior VPN.
Below we will deepen the concept through a section dedicated to the topic.
Connectivity
We will now deal with the basis for operating in Remote Working : connectivity.
Bandwidth consumption
Once our remote devices are connected to the VPN, they will, from a logical point of view, be physically connected to the company network, passing through the Internet connection of both the company and the remote device.
Obviously, it follows that the maximum speed of the VPN channel will be given by the lower speed between the 2.
You should also know that the RDP protocol (or its derivatives) has been designed to optimize the flow of data.
Other protocols used for file sharing, data transfer, database connection, and many others, are NOT at all optimized to be used between remote devices and risk creating many headaches for those who use them.
Therefore, its use is strongly discouraged.
Making a distinction between all protocols is not a simple thing, for this reason we decided to deepen the setup and configuration using the RDP protocol which eliminates the problem at the root, completely excluding the problem.
We have conducted studies to measure the ACTUAL bandwidth consumption for each VPN + RDP connection and below we present the most significant data:
Bandwidth consumption for remote users using OpenVPN and RDP:
- minimum consumption: (using office applications) 25-50 KBits / sec or 200 – 400 Kbit / sec
- average consumption: 50-70 KBits / sec or 400 – 560 Kbit / sec
- high consumption: (video and audio streaming) 1-4 MBits / sec or 8 – 32 Mbit / sec
Remembering that: 1 Byte = 8 bits
If you intend to work remotely in file sharing, you should know that the hypothesized data flow should be multiplied by a factor of 10 to 50.
To establish how much bandwidth we need we can set the following calculation:
Optimal Total Band = band required by the company headquarters + n. users X 100 * KBits
* (from 70 KBits we round up to 100 KBits).
As for remote devices that perform office work (office applications) we can consider a connection of 50-70 KBits / sec (400 – 560 Kbit / sec) sufficient.
Sizing
As a prerogative, stable connectivity is essential to guarantee the fluidity necessary for the performance of Remote working.
By stable connectivity we mean a flow of data that is not subject to fluctuations caused by external factors such as excessive load of the global network that typically occurs at times of greater load of the network.
Here are some operational tips:
- At company level it is necessary to choose a good bandwidth both in DOWNLOAD and in UPLOAD as data from users who work remotely on the various Servers could be both loaded and downloaded using the various applications or simply working on network folders.
- This network will have to manage the various remote connections from the clients via the VPN and will have to be sized according to the amount of data managed and the number of connected users.
- Where possible, an FTTH or FTTC fiber optic connection is the best solution on the company side, while for remote devices it will be sufficient to have a less performing connection. On the company side, it is essential to have a fixed Public IP address or even better a pool of addresses provided by the Provider so that we can assign the IP address directly on the Firewall that will act as a server for our VPNs.
- Whether you have a single fixed IP or a pool, it is necessary to have the possibility, if necessary, of opening the router side ports of our Provider necessary for the operation of the VPN connections.
- It would be a good idea to have a second backup network that comes into operation when the main network is down. However, this second connectivity is not essential. At the network level of remote users the same rules of the corporate network may apply, obviously in this case the amount of data will be lower but it is advisable not to underestimate the upload always for a matter of data upload.
Low-performing Wifi and mobile hotspots can be a temporary solution but can hardly be a good solution in the long run.
Transformation
Now let’s define the other steps to be taken to transform our old-fashioned company.
Since there are many topics and of varying difficulty, we have preferred, from here on, to divide the guide into small technical articles that deal with distinct topics, so that the reader can skip “pieces” if he already has sufficient knowledge to perform the settings. independently.
Now let’s prepare our pfSense firewall and configure the VPN server.
Once the VPN configuration has been carried out, we proceed to configure the company’s PCs:
We set the fixed IP on the PC.
Let’s check the Windows power saving settings: https://blog.miniserver.it/en/firewall/pfsense-opnsense-and-3cx-accelerate-smart-working-using-free-tools-such-as-vpn-rdp-and-webmeeting/
We check the settings of the Windows firewall to allow access in RDP
Now let’s connect to the corporate network:
Let’s connect with OPENvpn from Windows PC: https://blog.miniserver.it/en/pfsense-and-openvpn-configuration-on-windows-pc/
Safety
Now that everything is up and running, let’s take care of improving and verifying the security of our solution. We absolutely cannot afford to compromise the security of our LAN.
To this proposal, we can first start to “tighten the links”, limiting access from outside users to only the servers or PCs to which they must access. But this may not be enough. To improve it further, we can set a VPN restriction at the hourly level. This allows us to allow access for some users only in certain time slots.
To learn more about aspects of access restrictions on VPN users: https://blog.miniserver.it/en/firewall/pfsense-and-openvpn-timed-access-for-openvpn-and-limitations-on-the-lan/
Now that we have limited access to the LAN, I want to test the security of the solution with a tool designed to do security analysis.
The following guide shows how to test the security of pfSense with OpenVas and thus generate detailed reports on the status of my solution.
If we extend the analysis not only to pfSense but to the entire corporate network, we will thus obtain a general report of the whole company in order to intervene in advance to resolve the problems reported.
Guide: https://blog.miniserver.it/en/pfsense/openvas-test-the-security-of-pfsense-opnsense-zeroshell-and-ipfire-with-the-vulnerability-assessment-system-the-most-famous-free-of-the-web/
In addition to OpenVPN there is also another technology for creating VPNs : IPsec.
Both pfSense and OPNsense implement it. This solution is also free and presents substantial differences both technologically and from a security point of view compared to OpenVPN.
We covered the discussion in this guide: https://blog.miniserver.it/en/pfsense/pfsense-and-vpn-differences-and-insights-on-ipsec-and-openvpn-security/
Choose the right device
The VPN introduces 2 elements that increase the CPU load, i.e. the encryption algorithm and data compression. The guide that follows examines these two aspects and compares their performance according to the algorithms present on pfSense, testing the performance of 2 hardware appliances of different ranges, offering ideas for choosing the hardware.
Guide: https://blog.miniserver.it/en/firewall/openvpn-and-pfsense-opnsense-optimization-of-encryption-and-traffic-compression-to-optimize-hardware-and-improve-security/
If you want a generic guide on hardware sizing that does not only take into account the VPN part, you can consult this complete guide to hardware sizing which deals with practically all the issues related to the workload of a firewall.
VoIP and WebMeeting
Now that all our users work remotely, we can convert our traditional PBX into a voip PBX with an extremely technological, simple to use and versatile tool, i.e. the 3CX solution.
3CX, allows among other things to do without the physical phone. This is not a trivial matter if we think in terms of economic savings. The solution allows us to install a software (called Softphone) that transforms our smartphone and / or our PC / notebook into a telephone station, thus allowing us to work as if we were in the office from anywhere in the world we find ourselves.
But that’s not all, always 3CX allows us to organize remote meetings (WebMeeting) always from our smartphone or PC wherever we are. All this for free.
The following guides show in detail how to install this solution:
Guide to the first configuration and be operational in a few minutes: https://blog.miniserver.it/en/3cx/3cx-guide-to-the-first-configuration-to-be-operational-in-a-few-minutes/
How 3CX WebMeeting works and what it does: https://blog.miniserver.it/en/3cx/3cx-webmeeting-the-free-3cx-solution-for-remote-meetings/
During the installation it will be necessary to modify the configuration of our pfSense to open the appropriate doors. The following guide guides you step by step.
Guide: https://blog.miniserver.it/en/firewall/3cx-pfsense-configuration-with-port-forwarding/