What we will see in this guide:
This guide illustrates how to assign a fixed IP (which can then be used in firewall rules) to a client that connects to a VPN, in particular OpenVPN, with a specific user.
This will allow me to create access rules for a user who logs into the VPN on the firewall.
Hardware and software environment
We carried out the tests in the laboratory with the pfSense system.
The hardware selected for the tests are:
Tested Firewall Datacenter:
For the VPN Firewall we chose this device: A1 Server
The software used on the appliance is pfSense® version 2.4.X
Introduction:
It is assumed that an OpenVPN server has already been created and one or more correctly configured users exist.
For a guide on how to create a VPN (OpenVPN) on pfSense follow the following guide: https://blog.miniserver.it/en/pfsense-and-openvpn-guide-to-creating-and-configuring-a-road-warrior-vpn-server/
For those who wish, we have also published a video that illustrates the steps we have performed below.
Let’s configure the Client Specific Overrides in OpenVPN:
First we identify an IP address that must belong to the VPN network that cannot be assigned to other users. In our example we know that a maximum of 10 users can connect; the assigned network is 10.10.94.0/24 and therefore we have chosen the IP 10.10.94.30
Subsequently, we precisely identify the user to whom we want to assign the IP just chosen, checking from System→User Manager→Users
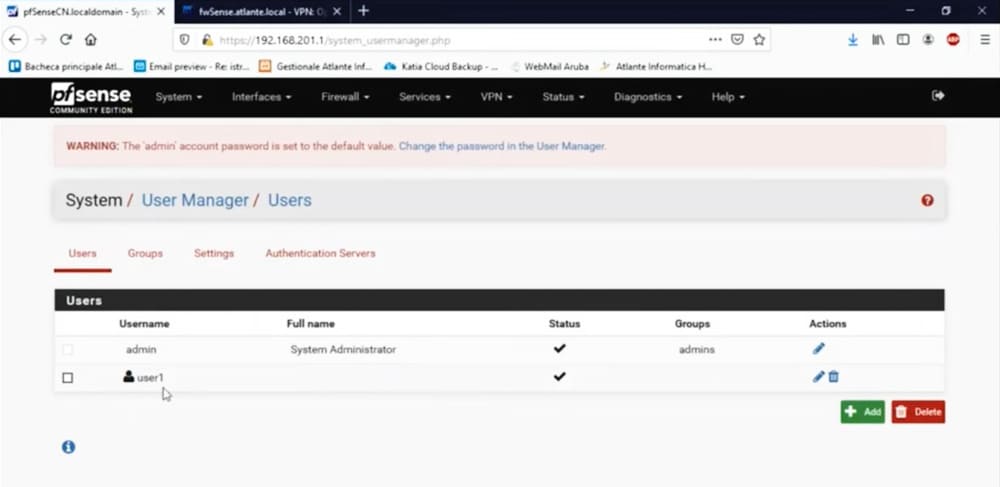
In our example: user1
At this point we position ourselves below
VPN→OPENVPN→Client Specific Overrides
And we add a voice.
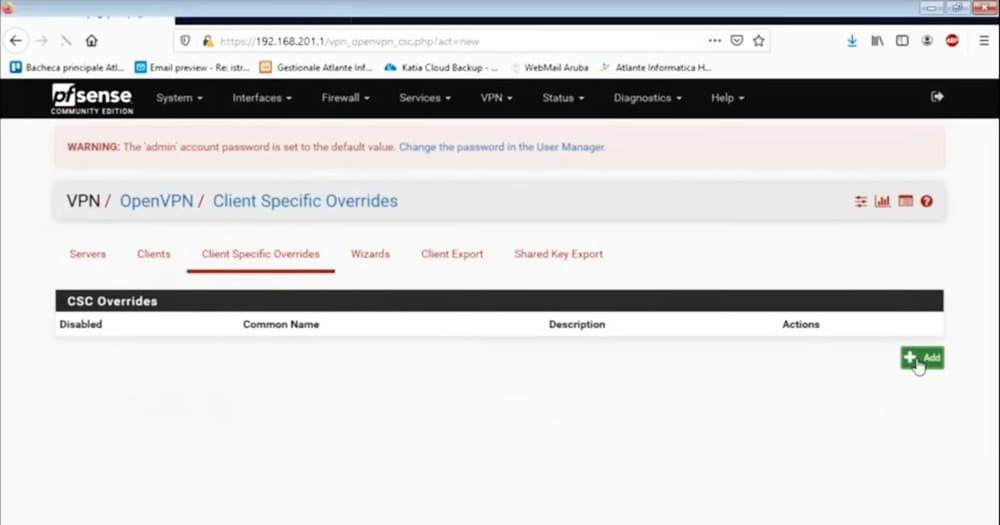
We select the desired openvpn server; in our case we only have one.
Then we write the exact name of the user in the “Common Name” field; in our example: user1
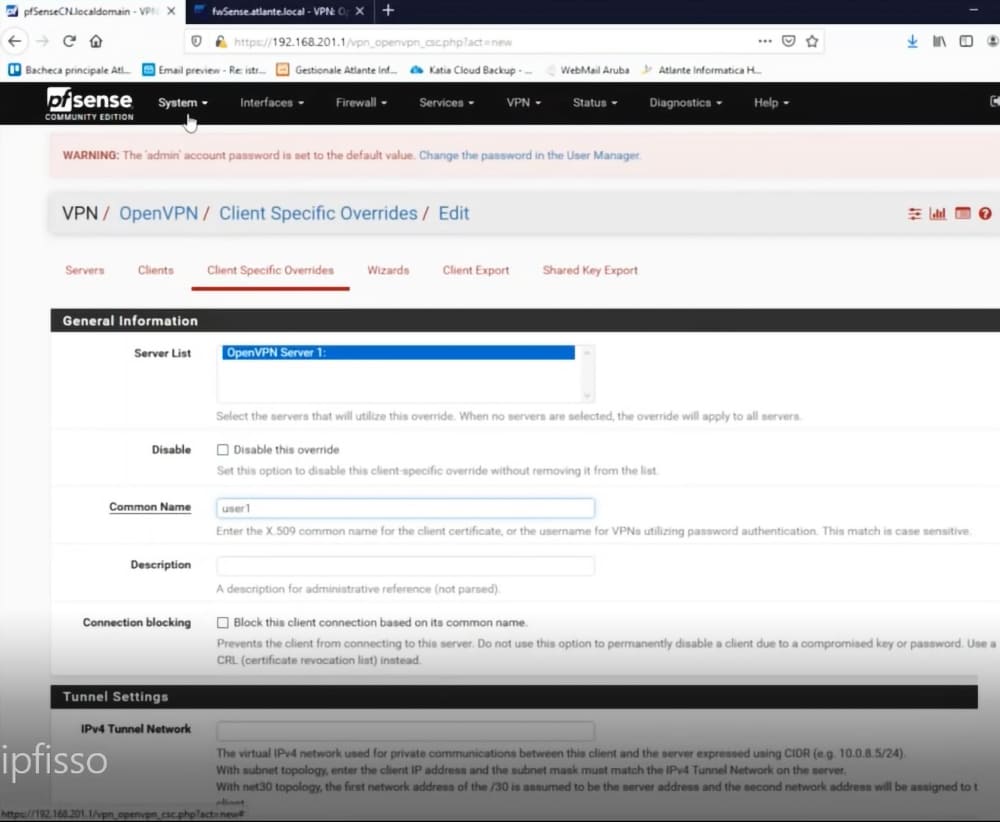
So let’s go to the bottom of the page and enter in advanced settings: ifconfig-push 10.10.94.30 255.255.255.0
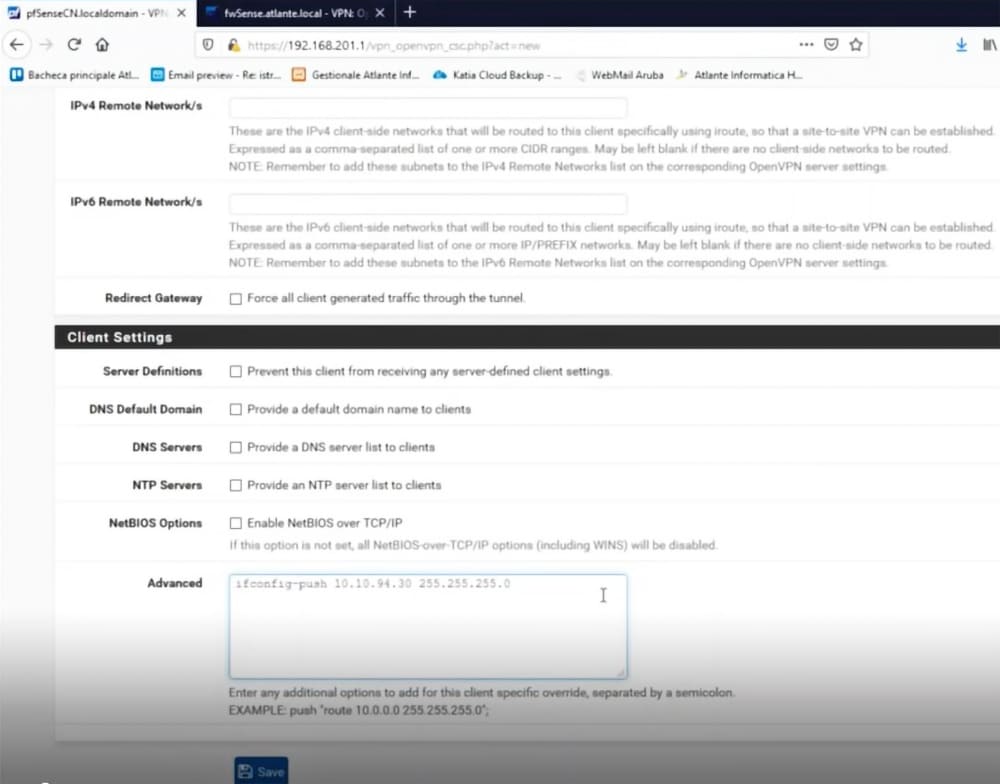
Even if we do not describe it here, if we want we can assign the ip DI to a completely different network, operating in the Tunnel settings section.
At this point we save. From now on when the user: user1 will connect to the OPENVPN VPN, he will always be assigned the IP 10.10.94.30
How we use this configuration in the rules
Once we know that user user1 will connect with IP 10.10.94.30, we can use this information to create our rules.
Let’s go under Firewall→Rules→OpenVPN
By placing the IP 10.10.94.30 in the Source field, we can decide which IP our VPN user can access and which ports/services.
In fact, they are exactly rules as if the OpenVPN interface were a physical interface and the user user1 was using a PC with a fixed IP.
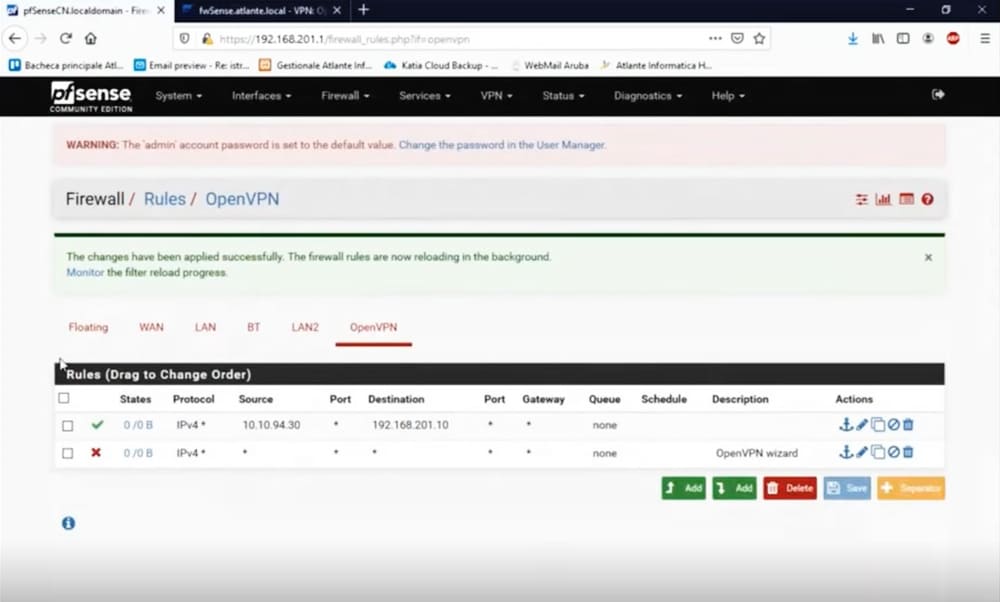
The rules above allow only the address 10.10.94.10, to access the IP 192.168.201.10 (in this example an IP of the LAN) on any port.
The remaining traffic will be blocked!
In our example, the last deny rule is actually not needed, we only put it to make explicit the deny which in fact is how the firewall behaves if no rule is applied.